Stealth addresses 101
A stealth address is a type of address that is used to protect the privacy of the recipient of a transaction. Stealth addresses are generated by the recipient of a transaction, and they allow the sender to securely transfer funds to the recipient without revealing their identity or the transaction details.
To create a stealth address, the recipient of a transaction generates a one-time public key. The sender then uses this one-time public key to create a special transaction that is sent to the recipient's stealth address. Because the one-time public key is only used once and is not linked to the recipient's regular address, the transaction remains private and secure.
Stealth addresses allow for the transfer of funds without revealing the identity of the recipient or the transaction details. This can be useful for transactions involving sensitive information, such as financial transactions or medical records.
How it works?
from 1000 feet..
The mechanics behind stealth addresses involves the use of elliptic curve cryptography. This is a type of cryptography that is based on the algebraic structure of elliptic curves over finite fields.
In the context of stealth addresses, the sender and recipient of a transaction each have a public key and a private key. The public key is derived from the private key using elliptic curve cryptography, and it can be used to encrypt and decrypt messages.
To generate a stealth address, the recipient generates a one-time public key that is derived from their regular public key using a process known as point multiplication. This one-time public key is then used by the sender to create a special transaction that is sent to the recipient's regular address.
The process of point multiplication involves multiplying the regular public key by a secret scalar value to generate the one-time public key. This scalar value is known only to the recipient, and it ensures that the one-time public key cannot be traced back to the recipient's regular public key.
By using elliptic curve cryptography and point multiplication, stealth addresses enable users to securely and efficiently transfer value without revealing their identities or transaction details.
The process for generating a stealth address using elliptic curve cryptography is as follows:
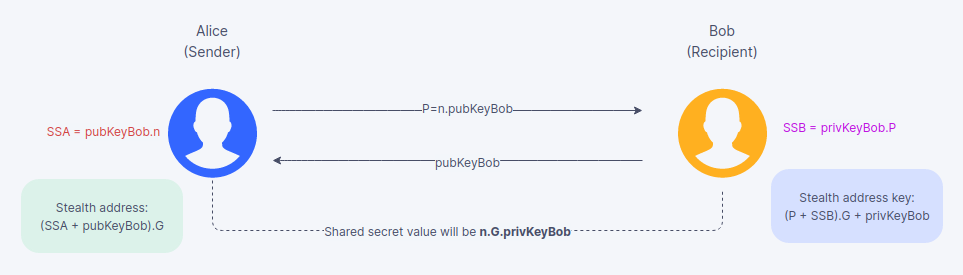
Consider 2 parties Alice and Bob. Alice is the sender and Bob is the recipient. The private key of Bob is privKeyBob and the public key of Bob is pubKeyBob which can be derived from privKeyBob.G.
G is the generator point on the elliptic curve.
n is a random nonce generated by Alice.
Bob shares his public key pubKeyBob to Alice and Alice generates a value P = n.pubKeyBob with Bob's public key and passes it back to Bob.
There will be a shared secret (SS) between Alice (SSA) and Bob (SSB), where SS will be same as SSA = pubKeyBob.n (privKeyBob.G.n) on Alice's end and SSB = privKeyBob.n.pubKeyBob. So both the values will be equivalent to the value privKeyBob.n.G
On Alice's end the stealth address can be calculated as: A' = (pubKeyBob + SSA).G
On Bob's end the key for stealth address can be calculated as: privKeyBob' = (P + SSB).G + privKeyBob
Now Bob can access the funds that was sent by Alice to the stealth address.
Overall, this process shows how a stealth address is generated and used to securely and privately transfer funds. By using elliptic curve cryptography and point multiplication, stealth addresses enable users to transfer value without revealing their identities or transaction details.
Acknowledgements and Further reading:
- Umbra protocol technical docs:https://app.umbra.cash/faq#how-does-it-work-technical
- Prof Bill Buchanan OBE's Medium article